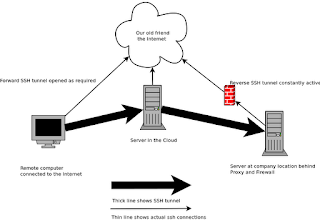
Well, how do we get this done. Read my previous article on how to set up tunnels using SSH, and once you have that up and running we can set up the VNC servers. Using Centos 6.2 as the server to connect to internally, running Gnome, install Tigervnc server and edit the /etc/sysconfig/vncservers and set your X session size, display port numbers and we wish to tell it to listen only to localhost. This is for security, we don't want it to respond to VNC on the actual IP address of the server.
Example:Start the vncserver , which will now be listening on port 5901 on localhost. Next off to the remote machine, where we need to set up the SSH config file so that it tunnels all VNC traffic through the SSH tunnel Go into .ssh/config and add the following for the remote user/machine
VNCSERVERS="1:nhaddock"
VNCSERVERARGS[1]="-geometry 1024x768 -localhost"
Host ext.server*
#HostName ext.server
User joeblogs
UserKnownHostsFile ~/.ssh/known_hosts.d/companyx
LocalForward 5901 localhost:5901
ProxyCommand ssh -A server.in-the-cloud exec nc localhost 10022
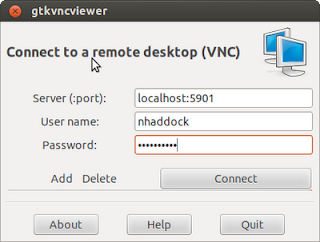
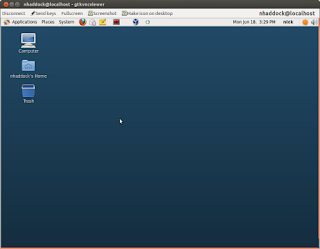
The key things to take away from this config, is that you need to add an entry in your /etc/hosts file for the ext.server IP address. We are going to forward all traffic for VNC - port 5901 into the tunnel once it is established using Localforward, and the proxy command uses netcat (nc) to push all the traffic down the reverse tunnel port it will find from your previous set-up with the reverse tunnel. So now just ssh to ext.server, and once you have made your connections, use a VNC viewer to connect to localhost on port 5901, and voila you now have an X session on the internal server.
Here are some pictures of the outcome.