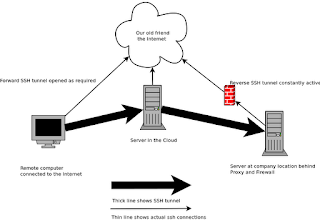
There is no doubt about it , the younger digital natives think Microsoft is the company of their parents, the tool they used for work and it's boring and out dated. This reasoning has taken a long time to come about, but with Apple ,Google and Linux constantly chipping away at the thinking that you need Microsoft to do anything it has finally taken hold, and I think for Redmond it is going to get a lot worse.
There is no doubt about it , the younger digital natives think Microsoft is the company of their parents, the tool they used for work and it's boring and out dated. This reasoning has taken a long time to come about, but with Apple ,Google and Linux constantly chipping away at the thinking that you need Microsoft to do anything it has finally taken hold, and I think for Redmond it is going to get a lot worse.You don't have to look far to see the signs of this , with young people using smartphones far more often than they use any other form of IT device. When they do turn to a laptop, they would prefer to use an Apple or Tablet than anything else. Windows 8 has not been the huge success it was supposed to be, and the Windows 8 Phone has been a complete flop plus the ARM based tablet has been slow to sell. To be honest , in a group of young people you will never see one in action, perhaps just the older IT users. That is part of the problem Microsoft is now seen as the old peoples platform , it's not what younger people want.
Now with the introduction of Bring Your Own Device - BYOD - into the corporate environment, Microsoft has never seen such pressure. People want to use their iPhone and Android phones to access the company data, and their tablets need to work too. They are far more likely to own an Apple, and these need to access the company network and data too. In the past they were given whatever the company wanted, normally with Microsoft , and they just used it. This is now not the case in a lot of cases, so people will not be forced to use anything they don't like.
An increasing large number of people are getting there work done, with the iPhone, iPad, Galaxy S III Android phone. I happily use Ubuntu Linux on the desktop, an iPad and an Android phone , with no Microsoft in sight. This is partly due to the switch to cloud based applications and the market dominance now of Google Chrome and Firefox. These are desktop platform neutral so you can run them on virtually anything. The availability of good apps on the other platforms that let you get work done has also increased, and will continue to become more compelling.
Some analysts are calling this the post PC era, and I can see for a large part of the population that is now true, and will increase. New tablet devices arrive almost daily from India and China at ever reduced prices, and Google is bringing the price of laptops down to rock bottom prices with Google Chromebooks. Smartphones are getting bigger screens and more powerful with each iteration, I can see docking stations for these devices becoming more popular.
The future will be different to what we have known in IT, and Microsoft will be playing a significantly reduced role in it. This is great, as I have never liked their monopoly , and active competition is good for the consumer.